Are you unsure of the validity of an email? We’ll discuss that shortly. But first, let’s think about how much email has incorporated into our lives, both personal and professional.
Hackers are having a field day robbing individuals of their hard-earned money as more people connect via email.
- Emails are a particularly appealing attack channel for cybercriminals for a number of reasons:
- You can get a free or cheap email account.
- Setting up an email account is easy for anyone.
- Sending many emails at once is simple.
- Emails arrive quite quickly.
- Computers, tablets, and other mobile devices with an internet connection can send and receive emails.
And if you believe that you are too intelligent to fall for an email scam, reconsider! Even the finest of us can fall prey to email scams, as history has repeatedly shown. Sounds absurd, right? That is, in fact, the case.
Email fraud scams have victimized businesses like Sony, Google, Facebook, Upsher-Smith Laboratories, and Ubiquity Networks. When huge corporations are attacked, millions of dollars are lost. Individuals and small-to-midsize businesses like us, however, could lose our hard-earned savings set aside for a rainy day if we fall victim to a swindle.
This is the reason it’s crucial that everyone understands how to determine if an email is authentic or not (legitimate).
How to spot Phishing E-mails
Sent from a public email domain
No legitimate company will ever send emails from a @gmail.com address. Even Google cannot.
With a few exceptions, most businesses will have their own email domains and business accounts. Emails from Google, for instance, will always begin with “@google.com.” The email is presumably real if the domain name, which is the part that comes after the @ sign, matches the email’s purported sender.
On the other hand, if the email originates from a different address than the apparent sender, it is almost probably a hoax. The easiest way to identify a fake email is if it comes from a sender with a public email address, such as “@gmail.com.”
Example:
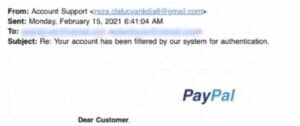
As you can see in this illustration, the email address of the sender does not match the message’s content, which purports to be from PayPal.
The attacker customized the sender’s name field so that it will display in recipients’ inboxes as “Account Support,” despite the fact that the message’s content appears to be realistic.
Other phishing emails will use a more complex strategy by incorporating the name of the organization in the local part of the domain. The email address, in this case, can be “[email protected].”
Because the email address contains the word “PayPal,” you might initially believe it to be authentic. But keep in mind that the part of the address that matters is what comes after the @ sign. The organization from which the email was sent is indicated by this.
You can be certain that an email has come from a personal account if it is signed with “@gmail.com” or another public domain.
The domain name is misspelled
Another hint that strongly suggests phishing scams is concealed in domain names, but it complicates the first one we found.
Anyone can purchase a domain name from a registrar, which is a concern. There are numerous ways to produce addresses that are identical to the one that is being faked, even though every domain name must be unique.
Example:
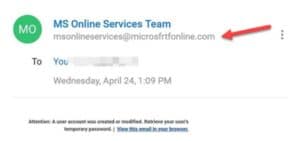
Here, scammers have registered the domain “microsfrtfonline.com,” which, to a casual reader, closely resembles the words “Microsoft Online” and might be mistaken for a real website.
The E-mail is illegible.
When an email has errors in spelling and language, you can usually tell that it is a fraud. Many people will tell you that these mistakes are a part of a “filtering system” that allows cybercriminals to only target the most trusting individuals.
According to the notion, if a person misses writing cues in communication, they’ll be less likely to notice cues throughout the con artist’s end goal. This, however, only applies to absurd schemes, such as the frequently parodied Nigerian prince scam, for which you would have to be extraordinarily gullible to fall for.
That fraud and others like it are manually carried out; after a victim takes the bait, the con artist must respond. Therefore, it is to the thieves’ advantage to limit the pool of replies to those who are likely to fall for the rest of the trick.
Phishing, however, is an exception to this.
It contains malicious attachments or dubious URLs.
There are several types of phishing emails. Although we’ve concentrated on emails in this piece, you might also receive scam texts, calls, or social media posts.
However, phishing emails always have a payload, regardless of how they are sent. It will either invite you to download an infected attachment or provide a link to a phony website.
These payloads are designed to collect private data, including login credentials, credit card information, contact information, and account numbers.
Example:
Suspected Links
The destination address of a link can be a red flag if it doesn’t make sense in the context of the email as a whole.
For instance, you would anticipate the link in an email from Netflix to take you to a website that starts with “netflix.com.”
Unfortunately, a lot of emails—both valid and scam—hide the destination address in a button, making it difficult to tell where the link will take you.
There is a sense of urgency in the message.
Scammers are aware that most people put things off. We decide to deal with an email that contains vital information later after receiving it.
But the more you consider something, the more probable it is that you will identify irregularities.
Perhaps you find out the company doesn’t use that email address to get in touch with you, or you ask a colleague if they received the document.
Even if you don’t have that “a-ha” moment, going over the message again with new eyes may reveal its full meaning.
Because of this, a lot of scams urge you to take action right now before it’s too late. Every example we’ve given so far has made this clear.
Regularly used services like PayPal, Windows, and Netflix could be negatively impacted right away by any issues.
Scams at work also use a contrived sense of urgency to their advantage.
When our boss emails us with a critical request, criminals are aware that we’re likely to put everything on hold, especially if other senior colleagues are ostensibly waiting for us.
Conclusion
The easiest method to safeguard your company from phishing scams is to inform staff members of how they operate and what to watch out for. Employees will be able to identify phishing attempts even as they get more complex with regular staff awareness training.
Your staff won’t be able to form healthy habits and recognize bad messages as instinctively necessary until you consistently reinforce the guidance on avoiding fraud.